Hackers launched a massive campaign to search the e-wallet Ethereum and equipment for mining. As the co-founder of “Bad Packets”, specializing in cyber security, mass scanning equipment proceeds from 3 December.
Attackers scan the device with the port 8545, which is available online. This is the standard port for the interface JSON-RPC many purses Ethereum and equipment for mining. This interface is a programmatic API through which locally installed applications and services can query for information concerning mining and foundations.
Theoretically, this API should only be available locally but some applications of the purse and equipment for mining include it on all interfaces. In addition, this interface JSON-RPC if it is included, by default, has no password, and it should be installed manually by the user.
If the Ethereum wallet or mining hardware is on a Network with an open port 8545, attackers can send a command to the theft of ETH with the address of the victim.
The problem with the port 8545 is not new. In August 2015, the Ethereum team is sent out to all users Ethereum safety advice about the dangers of using equipment for mining and Ethereum software, which provides access to this API via the Internet, and encouraged users to take precautions, adding the password in the interface or use a firewall to filter inbound traffic on port 8545.
Many suppliers of mining equipment and manufacturers of applications for purses took precautions, limiting access to the port 8545, or even removed the interface JSON-RPC. Many, but not all.
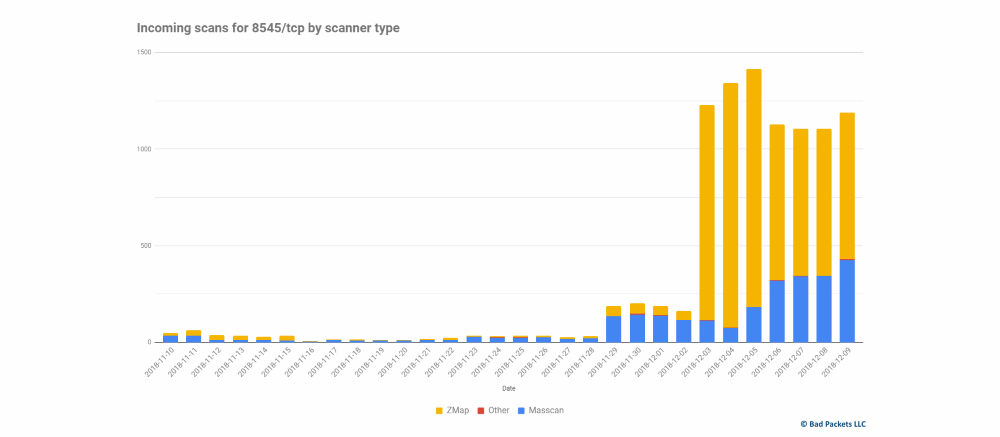
To understand the scale of the problem, note that only a quick search using the Shodan service detects approximately 4,700 units, most of which — mining equipment Geth and purses Parity that currently have open port 8545.
.

